Git Version Control
Publ .
Mins 12 (2494 words).
Edit .
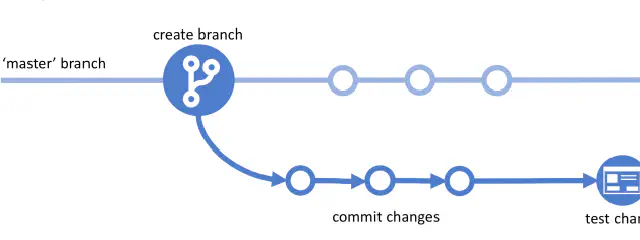
The last levels take a dive into an essential tool that every software developer must master. Git version control.
git is a widely used distributed version control system, that allows
developers to track changes in their code, collaborate with others, and manage
different versions of their projects. It offers many features, and can be used
to manage code for small and large projects. Understanding the basics of git
and later on, branching may give a future developer the skill needed to
effectively manage a codebase and collaborate with others.
On a side note, you should not confuse Git with GitHub. The latter is a private web-based platform that utilizes Git, and provides additional features such as issue tracking, documentation, and project management.
gitis not installed by default on all Linux distributions, but can be easily installed through package managers.
Understanding the very basics of Git may be a daunting task, here are some of the sources that surely help at accomplishing the objective:
The official Git documentation has a “Getting Started” section that provides a great introduction to the basic Git commands: https://git-scm.com/book/en/v2Getting-Started-Git-Basics
GitHub has a tutorial that covers the basics of Git in a very simple and easy-to-follow way: https://try.github.io/
Index
LEVEL 27 -> LEVEL 28
There is a git repository at
ssh://bandit27-git@localhost/home/bandit27-git/repo. The password for the userbandit27-gitis the same as for the userbandit27.Clone the repository and find the password for the next level.
Commands you may need to solve this level
git
Assuming that the basic information and instructions about git have been read
and understood, let’s create a new directory to hold the cloned objects from the
given repository:
$ mkdir /tmp/foobarbaz
cd /tmp/foobarbaz
The command to fetch remote objects is git clone followed by the address of
the repository to clone. There is a little caveat. The address given is:
ssh://bandit27-git@localhost/home/bandit27-git/repo lacks a reference to the
port that ssh is using on this server. Used as given the commands fail. You
must complete the schema by adding the string :2220 to the second segment of
the URL.
$ git clone ssh://bandit27-git@localhost:2220/home/bandit27-git/repo
Cloning into 'repo'...
The authenticity of host '[localhost]:2220 ([127.0.0.1]:2220)' can't be established.
ED25519 key fingerprint is SHA256:C2ihUBV7ihnV1wUXRb4RrEcLfXC5CXlhmAAM/urerLY.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Could not create directory '/home/bandit27/.ssh' (Permission denied).
Failed to add the host to the list of known hosts (/home/bandit27/.ssh/known_hosts).
_ _ _ _
| |__ __ _ _ __ __| (_) |_
| '_ \ / _` | '_ \ / _` | | __|
| |_) | (_| | | | | (_| | | |_
|_.__/ \__,_|_| |_|\__,_|_|\__|
This is an OverTheWire game server.
More information on http://www.overthewire.org/wargames
bandit27-git@localhost's password:
When asked, just issue the password for user bandit27-git.
remote: Enumerating objects: 3, done.
remote: Counting objects: 100% (3/3), done.
remote: Compressing objects: 100% (2/2), done.
remote: Total 3 (delta 0), reused 0 (delta 0), pack-reused 0
Receiving objects: 100% (3/3), 287 bytes | 287.00 KiB/s, done.
Once the procedure is completed you can explore the copied files.
$ ls
repo
$ cd repo/
ls
README
The README file contains the password for the next level:
$ cat README
The password to the next level is: AVanL161y9rsbcJIsFHuw35rjaOM19nR
Before moving on, clean the place: cd ~; rm -r /tmp/foobarbaz.
LEVEL 28 -> LEVEL 29
There is a git repository at
ssh://bandit28-git@localhost/home/bandit28-git/repo. The password for the userbandit28-gitis the same as for the userbandit28.Clone the repository and find the password for the next level.
Commands you may need to solve this level
git
Let’s create again a folder to use as placeholder and clone the repository:
$ mkdir /tmp/foobarbaz
$ cd /tmp/foobarbaz
$ git clone ssh://bandit28-git@localhost:2220/home/bandit28-git/repo
Cloning into 'repo'...
The authenticity of host '[localhost]:2220 ([127.0.0.1]:2220)' can't be established.
ED25519 key fingerprint is SHA256:C2ihUBV7ihnV1wUXRb4RrEcLfXC5CXlhmAAM/urerLY.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Could not create directory '/home/bandit28/.ssh' (Permission denied).
Failed to add the host to the list of known hosts (/home/bandit28/.ssh/known_hosts).
_ _ _ _
| |__ __ _ _ __ __| (_) |_
| '_ \ / _` | '_ \ / _` | | __|
| |_) | (_| | | | | (_| | | |_
|_.__/ \__,_|_| |_|\__,_|_|\__|
This is an OverTheWire game server.
More information on http://www.overthewire.org/wargames
bandit28-git@localhost's password:
remote: Enumerating objects: 9, done.
remote: Counting objects: 100% (9/9), done.
remote: Compressing objects: 100% (6/6), done.
remote: Total 9 (delta 2), reused 0 (delta 0), pack-reused 0
Receiving objects: 100% (9/9), done.
Resolving deltas: 100% (2/2), done.
There is no password on the files of the repository.
$ ls repo/
README.md
$ cat repo/README.md
# Bandit Notes
Some notes for level29 of bandit.
## credentials
- username: bandit29
- password: xxxxxxxxxx
The readme contains a line exclusively dedicated to the password for user
bandit29. But that string is not a valid password. Let’s use the git log
command to explore the history of the repository and understand how it has
evolved over time. This command is helpful for tracing the origin of changes.
$ cd repo
$ git log
commit c6dc61e6ffdc717253130886555d087cac472f50 (HEAD -> master, origin/master, origin/HEAD)
Author: Morla Porla <morla@overthewire.org>
Date: Wed Jan 11 19:18:53 2023 +0000
fix info leak
commit 2c1f82f75ab09c89166dd9e6e351bf479fb2d48f
Author: Morla Porla <morla@overthewire.org>
Date: Wed Jan 11 19:18:53 2023 +0000
add missing data
commit 444da53e268c462d39cf7441a3bbf7af1832e21f
Author: Ben Dover <noone@overthewire.org>
Date: Wed Jan 11 19:18:53 2023 +0000
The commits appear in reverse chronological order. The last one has as message
fix info leak. It may be the case that the maintainer of the repository had
swapped the plaint text password for the current string.
To explore how the repository was and navigate through it in a previous
state, you use the checkout command followed by the desired commit hash. You
can think about this feature as going ‘back in time’.
$ git checkout 2c1f82f75ab09c89166dd9e6e351bf479fb2d48f
Note: switching to '2c1f82f75ab09c89166dd9e6e351bf479fb2d48f'.
You are in 'detached HEAD' state. You can look around, make experimental
changes and commit them, and you can discard any commits you make in this
state without impacting any branches by switching back to a branch.
If you want to create a new branch to retain commits you create, you may
do so (now or later) by using -c with the switch command. Example:
git switch -c <new-branch-name>
Or undo this operation with:
git switch -
Turn off this advice by setting config variable advice.detachedHead to false
HEAD is now at 2c1f82f add missing data
As the message reads, you can now explore the contents and see the previous
state of the README.md file, when it still leaked the password string:
$ cat README.md
# Bandit Notes
Some notes for level29 of bandit.
## credentials
- username: bandit29
- password: tQKvmcwNYcFS6vmPHIUSI3ShmsrQZK8S
LEVEL 29 -> LEVEL 30
There is a git repository at
ssh://bandit29-git@localhost/home/bandit29-git/repo.The password for the userbandit29-gitis the same as for the userbandit29.Clone the repository and find the password for the next level.
Commands you may need to solve this level
git
Again let’s create a temporary folder and clone the repository into it:
$ mkdir /tmp/foobarbaz
$ cd /tmp/foobarbaz
git clone ssh://bandit29-git@localhost:2220/home/bandit29-git/repo
Cloning into 'repo'...
...
Receiving objects: 100% (16/16), 1.44 KiB | 1.44 MiB/s, done.
Resolving deltas: 100% (2/2), done.
Performing an inspection of the commit log, shows no evidence that may lead to a solution. The downloaded files:
$ ls -lah
total 16K
drwxrwxr-x 3 bandit29 bandit29 4.0K Jan 21 14:41 .
drwxrwxr-x 3 bandit29 bandit29 4.0K Jan 21 14:41 ..
drwxrwxr-x 8 bandit29 bandit29 4.0K Jan 21 14:41 .git
-rw-rw-r-- 1 bandit29 bandit29 131 Jan 21 14:41 README.md
$ cat README.md
# Bandit Notes
Some notes for bandit30 of bandit.
## credentials
- username: bandit30
- password: <no passwords in production!>
The README.md clearly says that there are <no passwords in production!>.
Let’s check if there are other branches for this repository. First, issue the
command git status to check the current branch. git branch -a will give you
a quick overview of all the branches available.
$ git status
On branch master
Your branch is up to date with 'origin/master'.
nothing to commit, working tree clean
git branch -a
* master
remotes/origin/HEAD -> origin/master
remotes/origin/dev
remotes/origin/master
remotes/origin/sploits-dev
There is a branch called origin/dev. This may stand for development
stage. This is usually the phase in software development where code is
written, tested and debugged to ensure it meets requirements and functions
correctly before it is ready for production.
Let’s “checkout to the development branch”. This action will change the files in the repository to the ones the code the developers have been be working on.
$ git checkout origin/dev
Note: switching to 'origin/dev'.
You are in 'detached HEAD' state. You can look around, make experimental
changes and commit them, and you can discard any commits you make in this
state without impacting any branches by switching back to a branch.
If you want to create a new branch to retain commits you create, you may
do so (now or later) by using -c with the switch command. Example:
git switch -c <new-branch-name>
Or undo this operation with:
git switch -
Turn off this advice by setting config variable advice.detachedHead to false
HEAD is now at be91af8 add data needed for development
The contents of the README markdown file, now have the password for the next level:
$ cat README.md
# Bandit Notes
Some notes for bandit30 of bandit.
## credentials
- username: bandit30
- password: xbhV3HpNGlTIdnjUrdAlPzc2L6y9EOnS
LEVEL 30 -> LEVEL 31
There is a git repository at
ssh://bandit30-git@localhost/home/bandit30-git/repo.The password for the userbandit30-gitis the same as for the userbandit30.Clone the repository and find the password for the next level.
Commands you may need to solve this level
git
Logging in, creating a temporary folder to hold the repository.
$ mkdir /tmp/foobarbaz
$ cd /tmp/foobarbaz
git clone ssh://bandit30-git@localhost:2220/home/bandit30-git/repo
Cloning into 'repo'...
......
bandit30-git@localhost's password:
remote: Enumerating objects: 4, done.
remote: Counting objects: 100% (4/4), done.
remote: Total 4 (delta 0), reused 0 (delta 0), pack-reused 0
Receiving objects: 100% (4/4), done.
A thorough inspection of the pulled folder reveals a README file only containing
a joke. git log is of no help. Also checking other branches for this
repository, yields nothing.
$ cd repo
$ ls -lah
total 16K
drwxrwxr-x 3 bandit30 bandit30 4.0K Jan 21 16:20 .
drwxrwxr-x 3 bandit30 bandit30 4.0K Jan 21 16:20 ..
drwxrwxr-x 8 bandit30 bandit30 4.0K Jan 21 16:20 .git
-rw-rw-r-- 1 bandit30 bandit30 30 Jan 21 16:20 README.md
$ cat README.md
just an epmty file... muahaha
$ git log
commit c027ef6d59c4031d56a6c6d16a526af0e8eb8383 (HEAD -> master, origin/master, origin/HEAD)
Author: Ben Dover <noone@overthewire.org>
Date: Wed Jan 11 19:18:56 2023 +0000
initial commit of README.md
git branch -a
* master
remotes/origin/HEAD -> origin/master
remotes/origin/master
Finally the solution comes by in a tag. In Git, a tag is a lightweight,
movable pointer to a specific commit. Tags are used to mark a specific point in
a repository’s history, such as a release version. Unlike branches, tags are
not updated as new commits are added to the repository.
$ git tag
secret
$ git show secret
OoffzGDlzhAlerFJ2cAiz1D41JW1Mhmt
LEVEL 31 -> LEVEL 32
There is a git repository at
ssh://bandit31-git@localhost/home/bandit31-git/repo.The password for the userbandit31-gitis the same as for the userbandit31.Clone the repository and find the password for the next level.
Commands you may need to solve this level
git
Cloning the repository.
$ mkdir /tmp/foobarbaz; cd /tmp/foobarbaz; git clone ssh://bandit31-git@localhost:2220/home/bandit31-git/repo
Cloning into 'repo'...
.....
Receiving objects: 100% (4/4), done.
Inspection
$ cd repo/
ls -lah
total 20K
drwxrwxr-x 3 bandit31 bandit31 4.0K Jan 21 17:09 .
drwxrwxr-x 3 bandit31 bandit31 4.0K Jan 21 17:09 ..
drwxrwxr-x 8 bandit31 bandit31 4.0K Jan 21 17:09 .git
-rw-rw-r-- 1 bandit31 bandit31 6 Jan 21 17:09 .gitignore
-rw-rw-r-- 1 bandit31 bandit31 147 Jan 21 17:09 README.md
Besides the usual README.md and the .git folder that tracks the repository’s
information, there is a file called .gitignore.
A gitignore is a plain text file that indicates Git files or directories to
ignore when committing changes. It can be used to ignore files containing
sensitive information, temporary and backup files, etc. In short it is an
artifact that tells git what should not be tracked in the repository.
Lets look at the contents of files:
$ cat .gitignore
*.txt
$ cat README.md
This time your task is to push a file to the remote repository.
Details:
File name: key.txt
Content: 'May I come in?'
Branch: master
The .gitignore file is set to not track files with txt extension.
The readme contains explicit instructions. You have to push a file named
key.txt whose content should be the string 'May I come in?' to the master
branch of the remote repository.
Creating the file and try adding it to the version control system:
$ echo "May I come in?" >> key.txt
$ git add key.txt
The following paths are ignored by one of your .gitignore files:
key.txt
hint: Use -f if you really want to add them.
hint: Turn this message off by running
hint: "git config advice.addIgnoredFile false"
Of course you can’t. All files of extension .txt are set to be ignored.
Let’s remove the .gitignore file and then proceed.
The complete process consists of adding the key.txt file, making a commit with
its respective message and finally pushing the changes to the master branch.
$ rm .gitignore
$ git add key.txt
$ git commit -m 'pushing a file to a remote repository'
[master 608e28a] pushing a file to a remote repository
1 file changed, 1 insertion(+)
create mode 100644 key.txt
$ git push origin master
The authenticity of host '[localhost]:2220 ([127.0.0.1]:2220)' can't be established.
ED25519 key fingerprint is SHA256:C2ihUBV7ihnV1wUXRb4RrEcLfXC5CXlhmAAM/urerLY.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Could not create directory '/home/bandit31/.ssh' (Permission denied).
Failed to add the host to the list of known hosts (/home/bandit31/.ssh/known_hosts).
_ _ _ _
| |__ __ _ _ __ __| (_) |_
| '_ \ / _` | '_ \ / _` | | __|
| |_) | (_| | | | | (_| | | |_
|_.__/ \__,_|_| |_|\__,_|_|\__|
This is an OverTheWire game server.
More information on http://www.overthewire.org/wargames
bandit31-git@localhost's password:
Enumerating objects: 4, done.
Counting objects: 100% (4/4), done.
Delta compression using up to 2 threads
Compressing objects: 100% (2/2), done.
Writing objects: 100% (3/3), 341 bytes | 341.00 KiB/s, done.
Total 3 (delta 0), reused 0 (delta 0), pack-reused 0
remote: ### Attempting to validate files... ####
remote:
remote: .oOo.oOo.oOo.oOo.oOo.oOo.oOo.oOo.oOo.oOo.
remote:
remote: Well done! Here is the password for the next level:
remote: rmCBvG56y58BXzv98yZGdO7ATVL5dW8y
remote:
remote: .oOo.oOo.oOo.oOo.oOo.oOo.oOo.oOo.oOo.oOo.
remote:
To ssh://localhost:2220/home/bandit31-git/repo
! [remote rejected] master -> master (pre-receive hook declined)
error: failed to push some refs to 'ssh://localhost:2220/home/bandit31-git/repo'